-
 chevron_right
chevron_right
Feds seize 13 more DDoS-for-hire platforms in ongoing international crackdown
news.movim.eu / ArsTechnica · Tuesday, 9 May, 2023 - 00:06
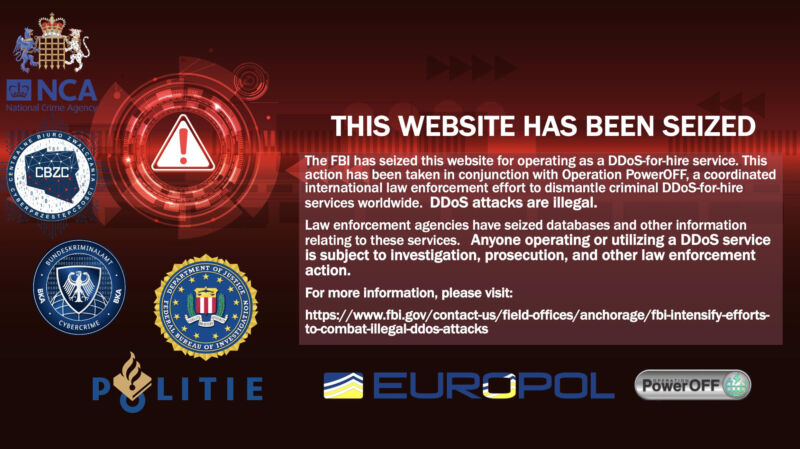
Enlarge / A domain seizure notice from the Justice Department, showing the national seals of several other governments.
The US Justice Department has sized the domains of 13 DDoS-for hire services as part of an ongoing initiative for combatting the Internet menace.
The providers of these illicit services platforms describe them as “booter” or “stressor” services that allow site admins to test the robustness and stability of their infrastructure. Almost, if not all, are patronized by people out to exact revenge on sites they don’t like or to further extortion, bribes, or other forms of graft.
The international law enforcement initiative is known as Operation PowerOFF. In December, federal authorities seized another 48 domains. Ten of them returned with new domains, many that closely resembled their previous names.





