-
chevron_right
Piracy Shield Source Code & Internal Documentation Leak Online
news.movim.eu / TorrentFreak · Tuesday, 26 March - 21:30 · 3 minutes
 Ever since Italian authorities announced their intent to introduce an even more aggressive anti-piracy blocking system than the one already in place, controversy has rarely been far behind.
Ever since Italian authorities announced their intent to introduce an even more aggressive anti-piracy blocking system than the one already in place, controversy has rarely been far behind.
Recent reports of avoidable overblocking, a reluctance to admit that the Piracy Shield system is fallible, and new reports that telecoms regulator AGCOM is now rejecting complaints from wrongfully blocked Cloudflare customers, are just some of the ingredients in a volatile mix that has always threatened to boil over.
Piracy Shield: Source Code Leaked Online
In what could develop into the biggest crisis yet for the Piracy Shield system and those who operate it, nine repositories of source code, internal documentation, and other related data, claiming to be the various components of the Piracy Shield system, appear to have leaked online.
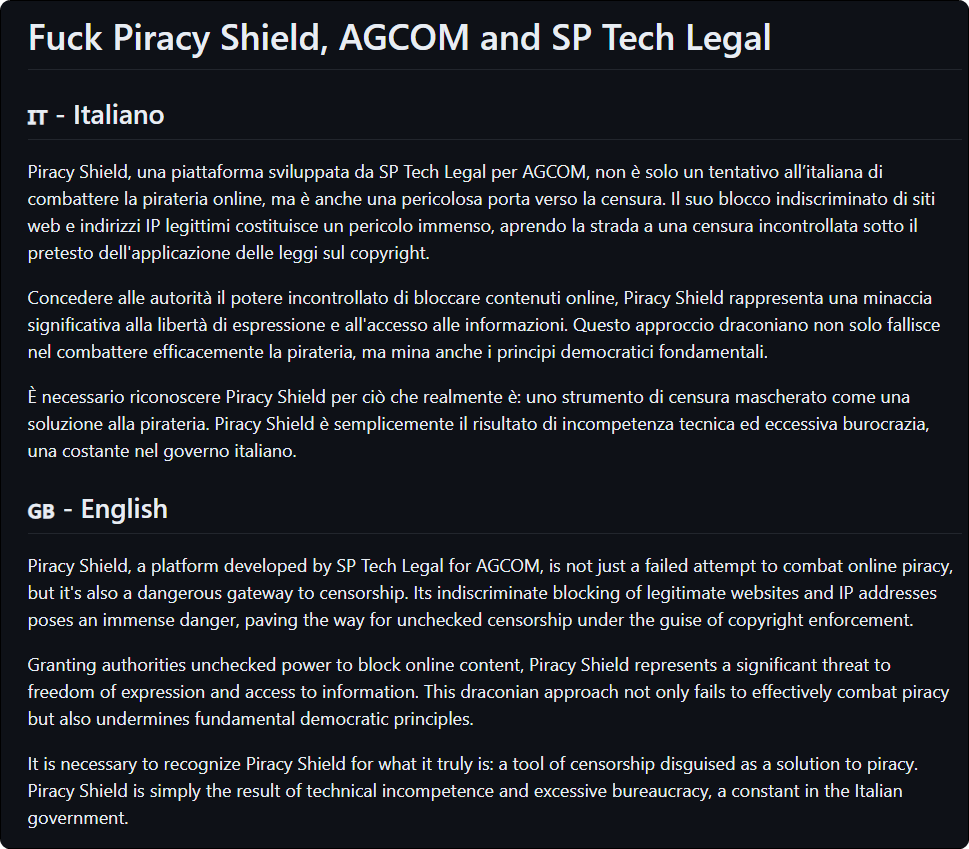
An announcement in Italian and English, posted on GitHub a few hours ago, criticizes AGCOM and SP Tech Legal, the law firm-linked developer behind Piracy Shield, for creating a “tool of censorship disguised as a solution to piracy.”
The main ‘fuckpiracyshield’ repository on GitHub was created by a user of the same name; they appear to have joined the site for the purposes of leaking the code online and, after signing up at 15:55 on Tuesday, by 16:50 they were gone. Aside from the leaked material, a message was left behind.
“This is not the way to stop piracy. This is a gateway to censorship,” the bio message reads.
Content Allegedly Leaked
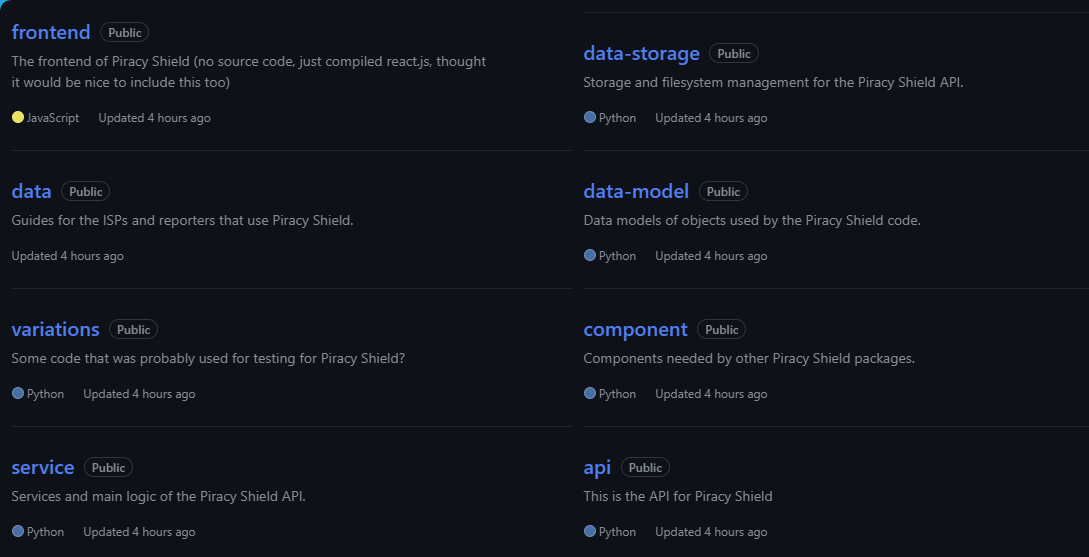
The apparently leaked collection spans nine repositories; they are named and described as follows:
frontend (The frontend of Piracy Shield), data (Guides for the ISPs and reporters that use Piracy Shield), variations (Some code that was probably used for testing for Piracy Shield?), service (Services and main logic of the Piracy Shield API), data-storage (Storage and filesystem management for the Piracy Shield API), data-model (Data models of objects used by the Piracy Shield code), component (Components needed by other Piracy Shield packages), api (This is the API for Piracy Shield)
For those unfamiliar with Python or no interest in code, period, the ‘data’ repository probably offers the most interesting information. It contains what appears to be up-to-date operations manuals for Piracy Shield, with the ‘ISP TECHNICAL MANUAL – PIRACY SHIELD’ described as v2.4.1, current on February 2nd when Piracy Shield made its full debut.
All documents are named and presented in Italian and the titles suggest that there are two versions of two distinct manuals: ‘Piracy Shield Manual’ and ‘Piracy Shield Error Codes’. One version seems to be directed at those reporting domains and IP addresses for blocking and the other toward the ISPs expected to carry out the blocking.
Unusual Feature of the Leak
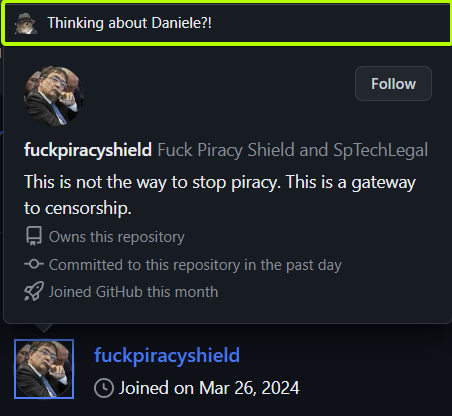
When browsing the source code and attempting to work out its purpose, on some repositories something immediately stands out. With no assumptions as to who the name refers, a contributor to the Piracy Shield project appears to be someone called Daniele Maglie. Their name appears time and again throughout the code, which in itself isn’t especially unusual.
However, when looking more closely at the leaker’s bio, which includes an image of AGCOM’s president apparently deep in thought, leaving the mouse pointer in place for a moment produces a piece of popup text, as highlighted in the image below.
What the text means, if indeed it means anything at all, will be just one of the questions being asked in the days to come. In the meantime, AGCOM has yet another blocking target to contend with, although a DMCA notice will be much more effective.
From: TF , for the latest news on copyright battles, piracy and more.