-
 chevron_right
chevron_right
“Worst cloud vulnerability you can imagine” discovered in Microsoft Azure
Jim Salter · news.movim.eu / ArsTechnica · Friday, 27 August, 2021 - 21:00

Enlarge / Cosmos DB is a managed database service offering—including both relational and noSQL data structures—belonging to Microsoft's Azure cloud infrastructure. (credit: Microsoft )
Cloud security vendor Wiz announced yesterday that it found a vulnerability in Microsoft Azure's managed database service, Cosmos DB, that granted read/write access for every database on the service to any attacker who found and exploited the bug.
Although Wiz only found the vulnerability—which it named "Chaos DB"—two weeks ago, the company says that the vulnerability has been lurking in the system for "at least several months, possibly years."
A slingshot around Jupyter
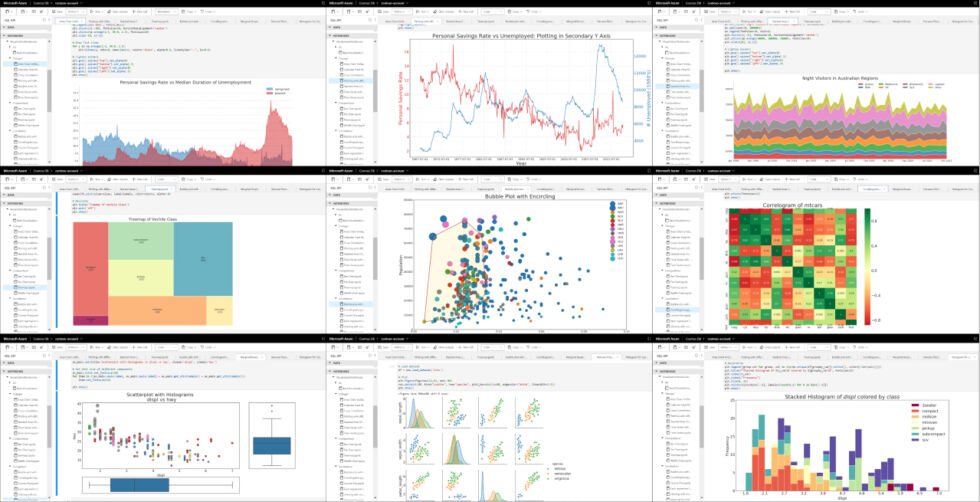
Jupyter notebook functionality in CosmosDB enables many advanced data visualization techniques with relatively little coding experience or effort. [credit: Wiz ]
In 2019, Microsoft added the open-source Jupyter Notebook functionality to Cosmos DB. Jupyter Notebooks are a particularly user-friendly way to implement machine learning algorithms; Microsoft promoted Notebooks specifically as a useful tool for advanced visualization of data stored in Cosmos DB.