-
 chevron_right
chevron_right
Movim 0.22 - Kowal
Timothée Jaussoin · pubsub.movim.eu / Movim · Sunday, 25 June, 2023 - 16:02 edit · 3 minutes
Only a few months after Movim 0.21 - Whipple we are releasing Movim 0.22, codename Kowal.
This version was more focused on stabilization, cleanup and refactoring but also introduces a couple of new exciting features. It requires PHP8.1+ to work properly.
Let's dive in!
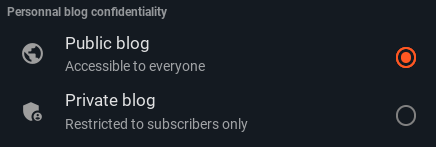
Blog privacy toggle
Already introduced in a previous blog post this new feature allow you to change your blog privacy level between "public" and "subscribers only".
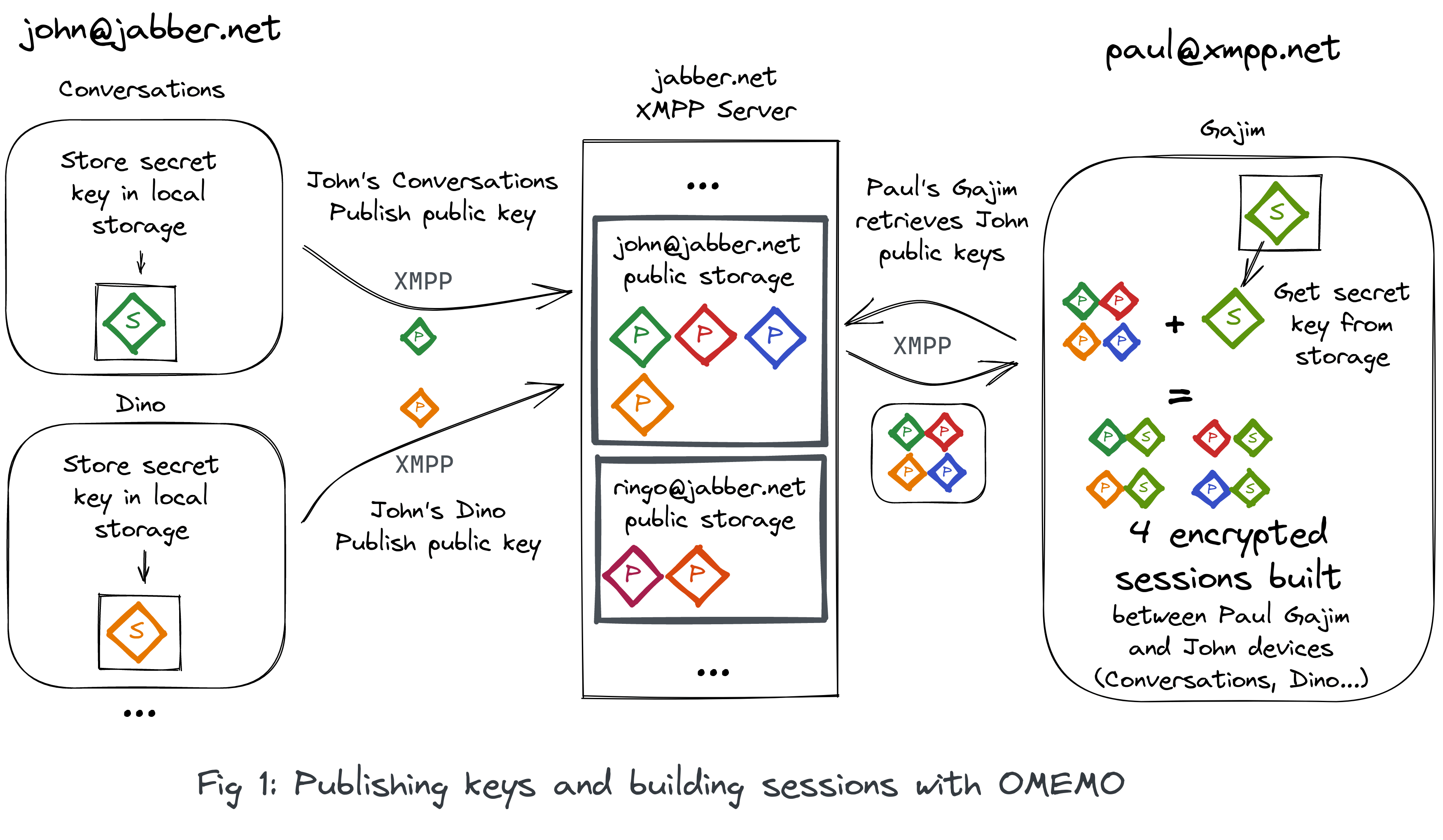
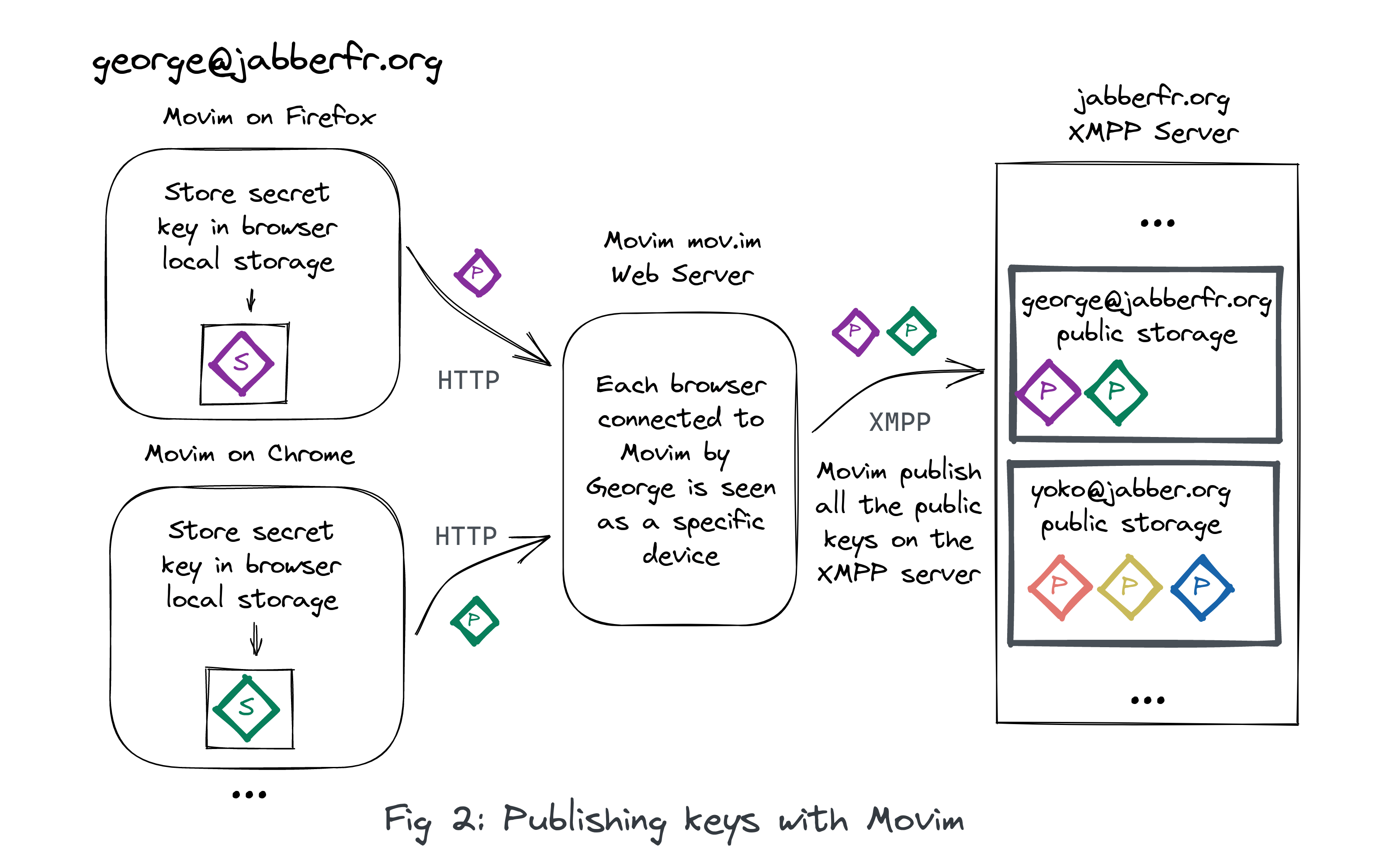
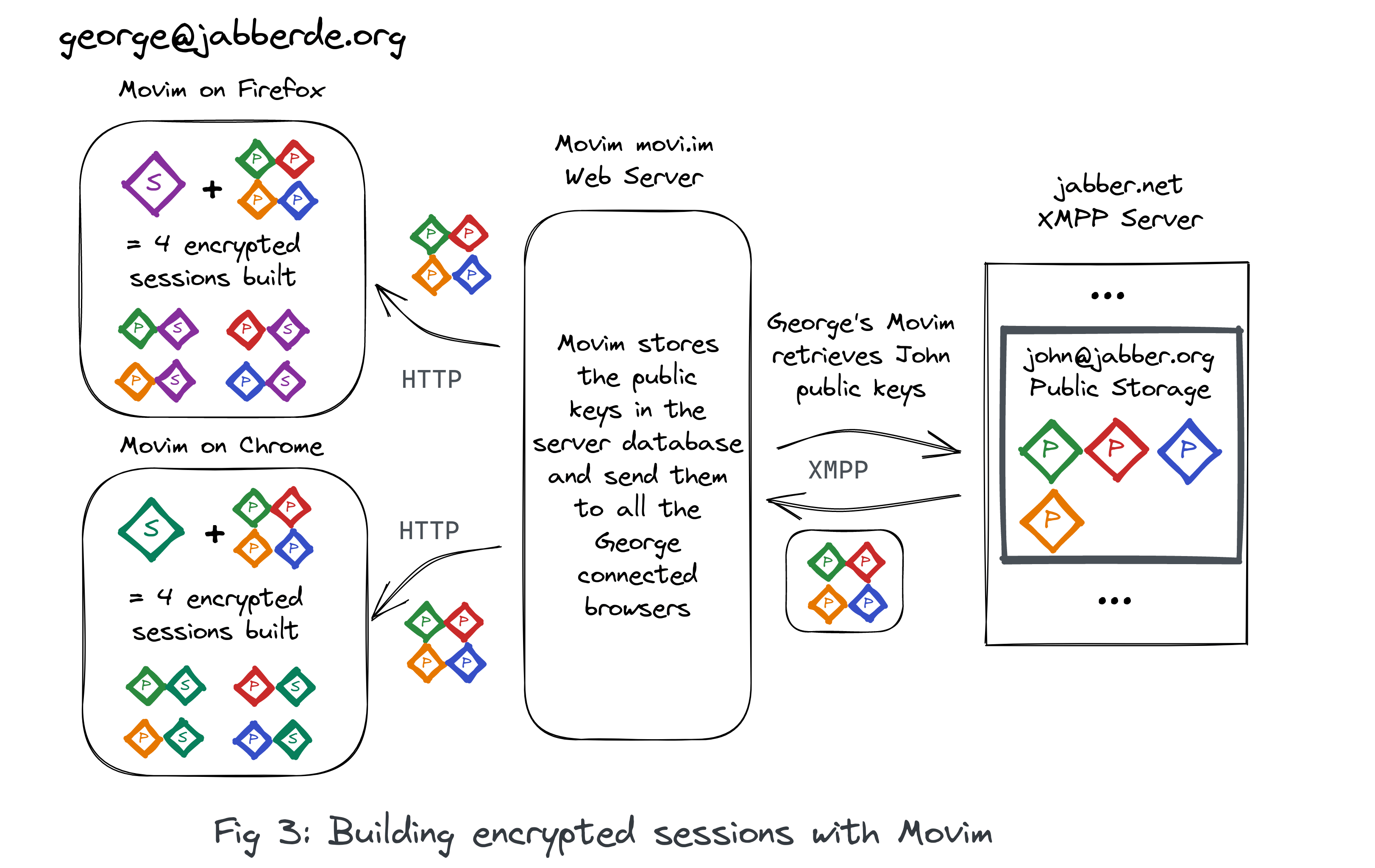
Global OMEMO toggle
After some feedback from the community a global #OMEMO toggle was introduced in the settings. OMEMO is therefore disabled by default from this version.
This decision is especially linked with the current encryption implementation that relies on libsignal-protocol-javascript that is deprecated by their authors. The performances of this library are not that great, especially on mobile devices, which caused lots of accessibility issues for some Movim newcomers.
For now, no serious alternative are available, if you know one do not hesitate to tell us about it.
Fixes and improvement around audio-video calls
Several small tickets (#1212, #1213, #1214) linked to the the audio-video call integration and compatibility with other clients were fixed.
Missed and refused call events are also now tracked properly and displayed in your contacts conversations.
Cleaner URLs
The ? was (finally) removed in front of all the URLs! While being way cleaner it also fixes some issues when #Movim URLs were shared around, especially on some other social-networks. Don't worry about retro-compatibility, existing URLs are redirected to the new format.
Rewrite of the XEP-0077: In-Band Registration related code
Movim is supporting XEP-0077 for close than 10 years now and this code was never really refactored since then. All the #XMPP code, and related user flow, were cleaned and upgraded to the latest Movim standard, fixing a few issues in the meantime!
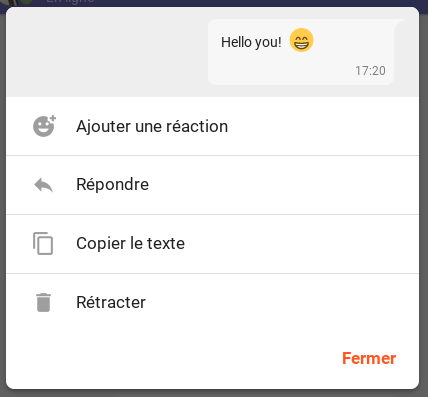
New Chat bubble design and interaction
Kowal introduce a totally new way of interacting with the chat bubbles.
While keeping the small actions icons on desktop it is now possible to simply click (or tap) on the bubbles to open a sub-menu which presents all the actions available.
This menu allows you to react, retract, reply and copy the message content in one click/tap. Easy!
Under the hood... or not
An important refactoring was done to simplify and factorize redundant items in the UI. This brought some big code cleanup, both on the front part (what is taking care of what you see) of Movim but also in the core and XMPP layers. The code was modernized and ported to PHP8.1+ in many places as well.
Several Pubsub related issues were fixed improving the compatibility with existing XMPP servers such as Prosody or ejabberd (see the related ticket). Movim now detect Pubsub nodes misconfiguration and reconfigure them properly to respect the privacy and settings specified in all the Pubsub related implemented XEPs that it supports.
This refactoring also brought some small UI improvements such as a new design for the contact status bubbles and a totally new way to handle Contacts and Communities avatars. We are strongly advising you to configure the Picture Proxy Cache on your Web Server when upgrading to greatly improve the page load time.
Two important security fixes
CVE-2023-2848 fixes a security issues that allows under certain circumstances to open a #Websocket to Movim from a different domain. It was fixed in this commit.
CVE-2023-2849 is not directly linked with Movim itself but the related server configuration.
When the domain that host upload files is the same as where Movim is hosted it is possible to upload a malicious Javascript file and execute it in the Movim sandbox. The attack surface is really minimal but we advise you to ensure that such case cannot happen on your instance. To do so you can use different domains between the two services or force the browser to handle all the uploaded files as attachments and not inline elements using a simple HTTP header:
add_header Content-Disposition attachment;
What's next?
The multi-part audio and video-conference feature that was planned for the 0.22 is pushed back to the 0.23. The amount of work planned for that is quite big, therefore it was more relevant to move all the code cleanup and refactoring plans in Kowal and have this milestone before jumping into this new exciting feature set !
As always, if you find issues or want to share some feedback you have on the project, you can find how to contact us on our official website and our Github.
That's all folks!