I was used to #release a new version of #Movim twice a year. Skiff is an exception. One year of work was required to release the 20th major version of the project.
The main reason is mostly based on the amount of work and adjustments required to integrate the main feature of this release: the support of end-to-end #encryption through the implementation of OMEMO.
So let's dive in all the new exciting features that you will discover in this major release.
OMEMO
The technical part was already extensively covered by the dedicated article End to end encryption in Movim - OMEMO is (finally) there!.
The user experience and flow is not very different than on other XMPP clients, if Movim detects that you can start an encrypted conversation with a contact a small lock icon will be displayed next to the chatbox. You can always choose to toggle it back to have a non-encrypted discussion.
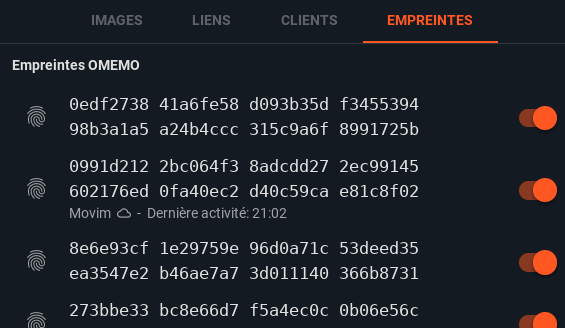
It is also possible to see all the encryption fingerprints in the Contact drawer under the dedicated "Fingerprints" tab. You can also enable and disable encryption to each fingerprint manually there. Movim is displaying the last message sent or received and the client linked to the fingerprint to help you with your configuration. But rest assured, those settings are only for those that wants to configure in detail their encryption levels.
End-to-end encryption is also available for group chats, the flow is exactly the same as for single contacts.
There is some chances that you encounter encryption issues in some cases, even after a lot of debug and refactoring end-to-end encryption is a really complex beast that is difficult to handle. Feel free to open a ticket with all the details to reproduce the issue if you encounter one.
I'd like to thank again NLNet for their help on this project ! With the funding I was able to free-up time to finally integrate end-to-end encryption in Movim.

Posts
A few changes were made regarding the posts and their integration within Movim.
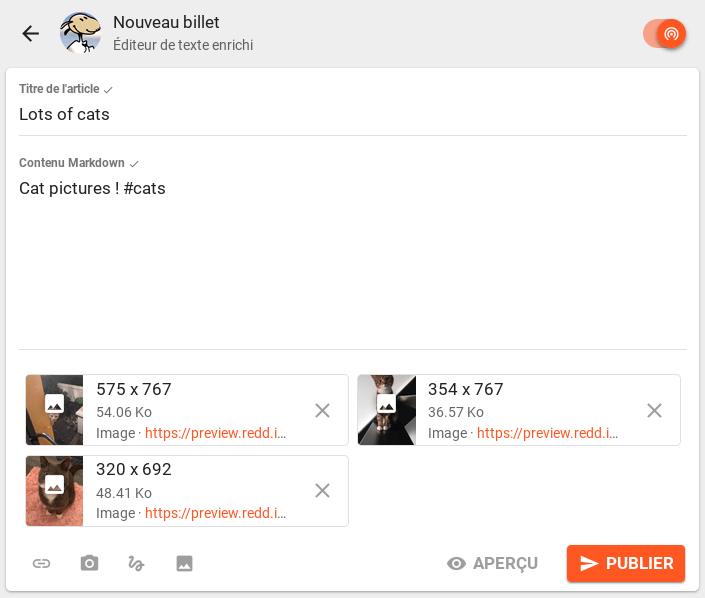
The post publication form was slightly redesigned and now allows several images, files or links to be attached.
Linked to that change, post cards were also redesigned with a more compact design.
The public Communities and Blog pages now have the same 2-columns design as their private version. The displayed Communities and Contacts information are also now more compact.
The tags were redesigned and are now more clearly visible and navigable.

Chat
The contacts and chatrooms drawers were redesigned and now include some really useful information. Pictures and links sent in conversations are now quickly available in dedicated tabs.
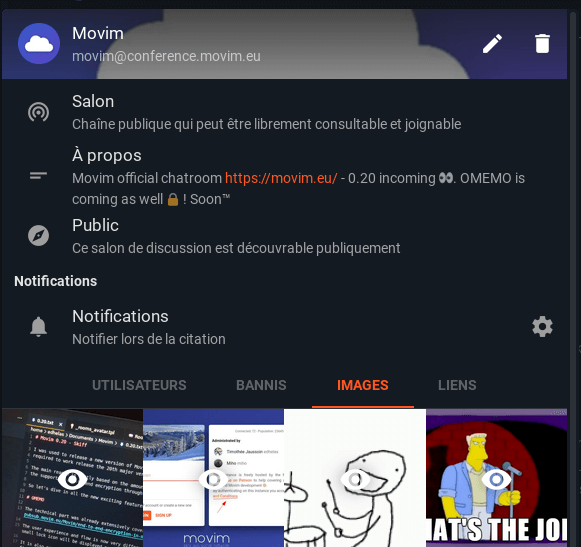
Chat bubbles are now properly displaying quotes and support message styling.
A big refactoring was also done regarding how the edited messages are handled in Movim. This refactoring allowed messages to be edited in Group Chats and the support of several edits on a single message (which caused some weird message duplication bug).
Chatrooms
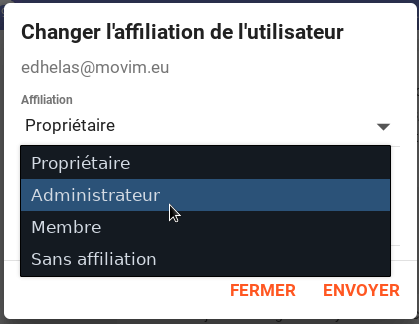
Chatrooms administrators can now manage affiliations and ban/unban users.
You can now prioritize your most important chatrooms on top of the list with the pin feature.
...and many other things
The old Movim API code was fully removed. It had been left untouched for years and not really used nor up-to-date anymore.
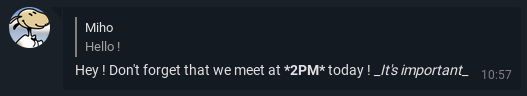
When you are in a chat conversation, the other chats counter is displayed on the back button.
The internal picture library was rewritten and simplified, it now supports transparent avatars. All pictures are now compressed in WebP by default.
Admins can now fully disable the registration feature. It is quite useful if you have a dedicated Movim setup and a specific separated flow to register your users (using an internal LDAP in a company or school for example).
Plenty of new emojis were integrated with the support of Unicode 13.0.
Movim is now a Progressive Web App
Movim used to have some "native" apps, on desktop and Android. All those app are now deprecated and replaced by work that was done to make Movim a full Progressive Web App. From any browsers you can now install Movim as an app on your phone or desktop in a single click.
Conclusion
Lots of other small improvements and features were integrated in this release but not listed there, it's time for you to discover them. Enjoy this new version!
That's all folks!
chevron_right