-
 chevron_right
chevron_right
PrivacyLens uses thermal imaging to turn people into stick figures
news.movim.eu / ArsTechnica · Thursday, 8 August - 21:36 · 1 minute
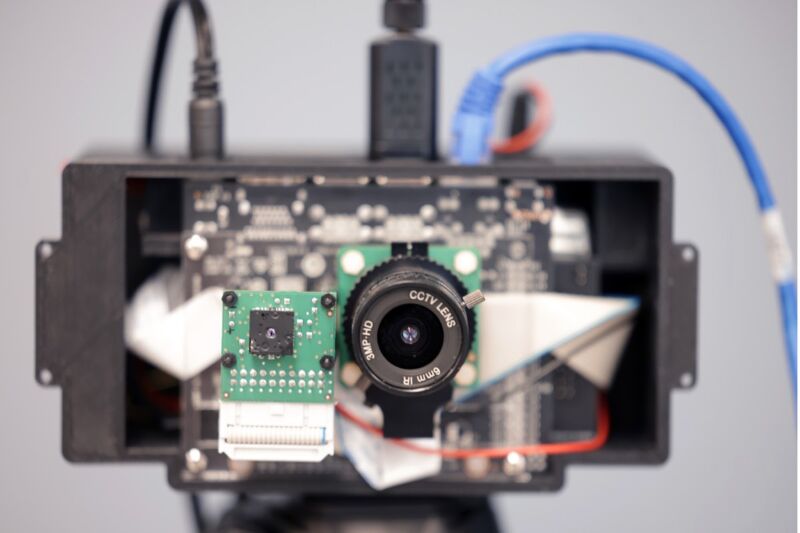
Enlarge / The round lens of PrivacyLens captures standard digital video while the square lens senses heat. The heat sensor improves the camera's ability to spot and remove people from videos. (credit: Brenda Ahearn, Michigan Engineering)
Roombas can be both convenient and fun, particularly for cats who like to ride on top of the machines as they make their cleaning rounds. But the obstacle-avoidance cameras collect images of the environment—sometimes rather personal images, as was the case in 2020 when images of a young woman on the toilet captured by a Romba leaked to social media after being uploaded to a cloud server. It's a vexing problem in this very online digital age, in which Internet-connected cameras are used in a variety of home monitoring and health applications, as well as more public-facing applications like autonomous vehicles and security cameras.
University of Michigan (UM) engineers have been developing a possible solution: PrivacyLens, a new camera that can detect people in images based on body temperature and replace their likeness with a generic stick figure. They have filed a provisional patent for the device, described in a recent paper published in the Proceedings on Privacy Enhancing Technologies Symposium, held last month .
"Most consumers do not think about what happens to the data collected by their favorite smart home devices. In most cases, raw audio, images and videos are being streamed off these devices to the manufacturers' cloud-based servers, regardless of whether or not the data is actually needed for the end application," said co-author Alanson Sample . "A smart device that removes personally identifiable information (PII) before sensitive data is sent to private servers will be a far safer product than what we currently have."
