-
chevron_right
Court Orders Cloudflare to Block and Identify ‘Pirate Site’ Customer
news.movim.eu / TorrentFreak · Saturday, 19 October - 16:30 · 4 minutes
 Internet infrastructure company Cloudflare provides a range of connectivity and security services to millions of customers around the globe.
Internet infrastructure company Cloudflare provides a range of connectivity and security services to millions of customers around the globe.
In addition to Fortune 500 companies and governments across various continents, the American company also provides its services to pirate sites.
In recent years, rightsholders have urged Cloudflare to take a more proactive stance against piracy. Their primary concern is that Cloudflare ‘hides’ the true hosting location of pirate sites, making enforcement actions more cumbersome.
Cloudflare takes a neutral stance, but it does cooperate in certain circumstances. The company has a process in place to disclose hosting information with eligible rightsholders, for example, and will also share details of allegedly pirating customers in response to DMCA subpoenas.
As far as we know, Cloudflare has not terminated any customers solely based on copyright holder complaints. This frustrated Italian broadcaster RTI up to the point where it decided to go to court.
RTI Sued Cloudflare over Pirate Site
April this year, RTI filed a complaint at the Court of Rome in an attempt to compel Cloudflare to take action against ‘Guardaserie’, a site that offers access to pirated TV streams. Guardaserie is already blocked by Italian ISPs, but it continues to operate and repeatedly switches to new domains to evade blocking actions.
Through the court, RTI wants Cloudflare to cease providing its services to Guardaserie and block all associated domain names. In addition, the broadcaster wants Cloudflare to reveal all information it holds that could help to identify the operator or operators.
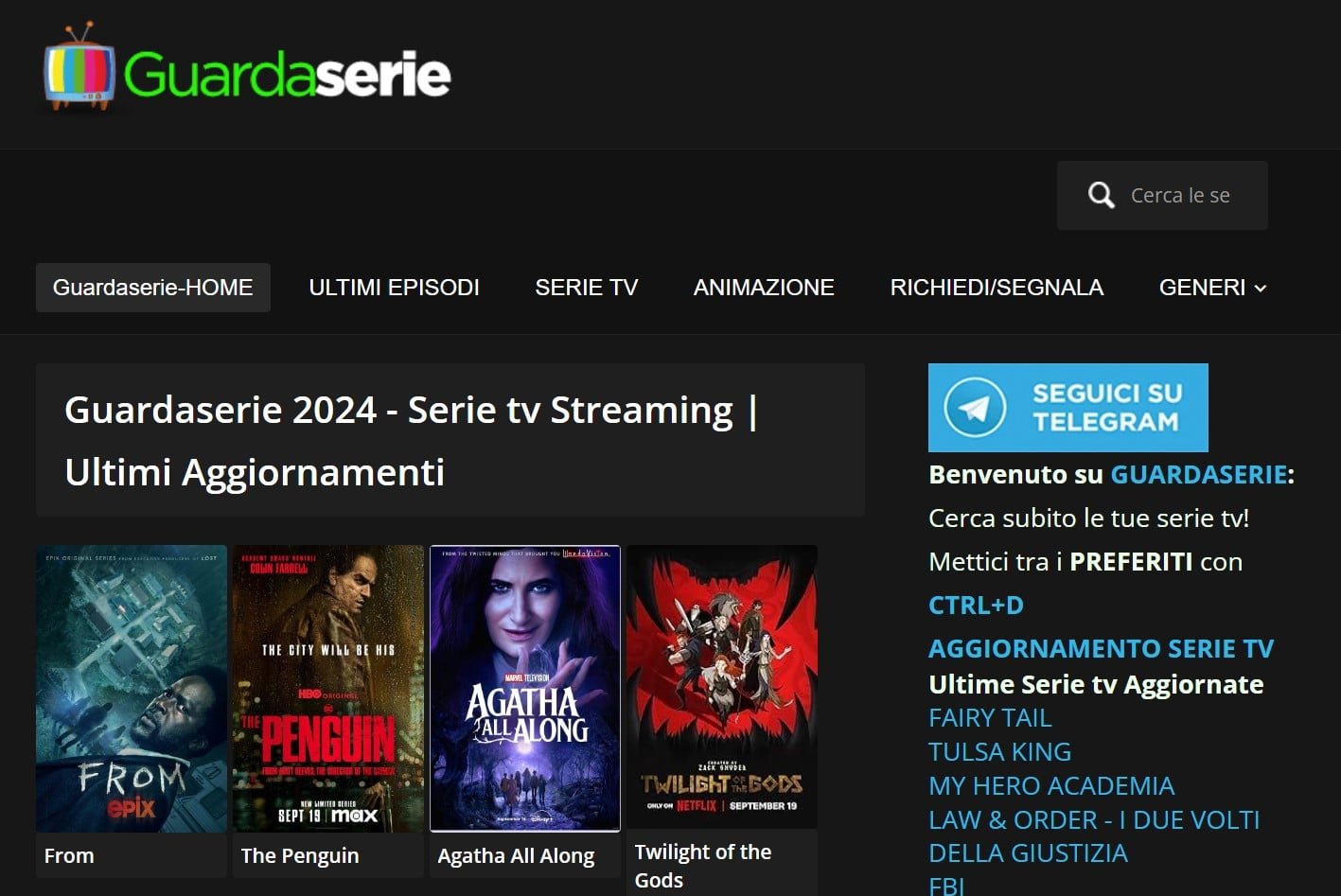
RTI informed the court that Cloudflare took no action in response to a cease and desist letter it sent earlier this year. According to the broadcaster, it is nonetheless undisputed that Guardaserie offers pirated content, which was backed up by an external report by the company SP Tech.
Cloudflare did not appear in court or present a defense against the allegations, but that didn’t stop the court from taking the matter forward.
Court Deems Cloudflare Liable
After reviewing the evidence, the Court of Rome agreed that the targeted website infringes Italian copyright law and that Cloudflare can be held liable due to its failure to respond to complaints.
According to the Court, Cloudflare’s inaction makes it harder for rightsholders to identify and block pirate sites.
“With respect to those infringements, it appears prima facie that the company Cloudflare inc. is a responsible intermediary pursuant to Article 156 of the Italian Copyright Law,” the decision reads.
“It provided services aimed at preventing the identification of the portals and the location of the servers of their owners, as well as technical support services to the portals, without taking any action to end those activities despite the cease and desist letter sent to it by the counterparty.”

Court: Disconnect, Block, and Identify Guardaserie
The Court of Rome ruled in favor of RTI and ordered Cloudflare to immediately cease providing services to Guardaserie. It further required Cloudflare to disclose any identifying account information connected to the operators of the infringing domains.
Guardaserie is a Cloudflare customer so, technically, domains should become unavailable through its services when the associated account is terminated. However, the court additionally orders Cloudflare to ‘block’ Guardaserie domain names.
And it doesn’t stop there.
The domain blocking order applies to all existing domain names, but also to domains that are registered in the future to bypass blocking measures. When RTI reports future domains to Cloudflare, these should be blocked as well.
“[The court] orders the blocking of said domain names that associate a different top-level domain with the same second level domain, burdening Cloudflare Inc. with notification to RTI of any additional names activated by Cloudflare accounts,” the order reads.
Cloudflare’s Stance
The Court of Rome’s order was issued late May but, as far as we know, hasn’t been publicly discussed until today. Cloudflare hasn’t mentioned it so far, and the company didn’t immediately respond to our request for comment.
At the time of writing, it appears that guardaserie.biz is still using Cloudflare’s nameservers that currently redirect to guardaserie.school. This new domain also uses Cloudflare nameservers.
Guardaserie.school leads to a partly broken website with missing content and a malware warning from Google, so the operators may have moved on by now. There are other domains using the Guardaserie brand that are still functional.
It’s possible that Cloudflare appealed the preliminary order, which could explain the apparent inaction, but we have no information to confirm that.
The Court of Rome’s order includes a penalty clause of €1,000 per day if Cloudflare doesn’t comply, so ignoring the order without proper cause could potentially come at a cost.
This is not the first time Cloudflare has faced legal action in Italy. The company was previously ordered to block pirate site domains though its 1.1.1.1 DNS resolver . It complied with this order by implementing a geo-block that only affects Italian users. An Italian court also ordered Cloudflare to terminate accounts of pirate customers in the past.
—
A copy of the Court of Rome’s order against Cloudflare is available here (pdf)
From: TF , for the latest news on copyright battles, piracy and more.
 The Alliance for Creativity and Entertainment (
The Alliance for Creativity and Entertainment (



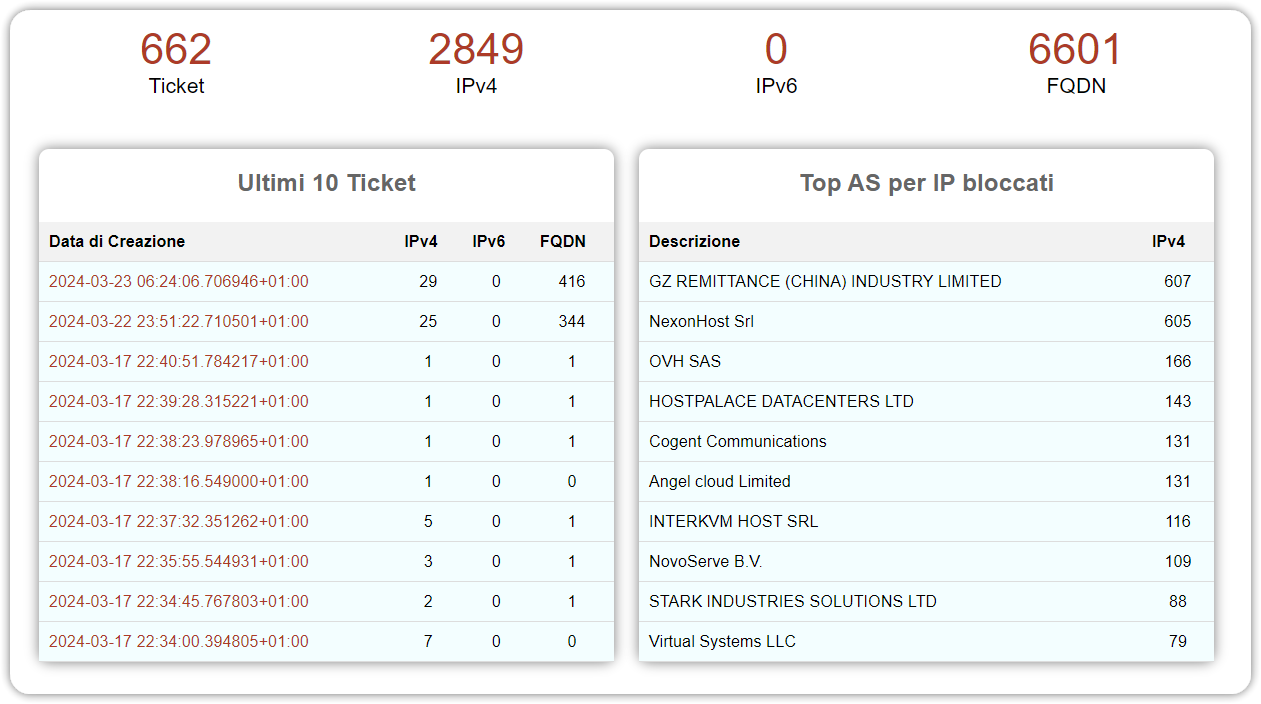
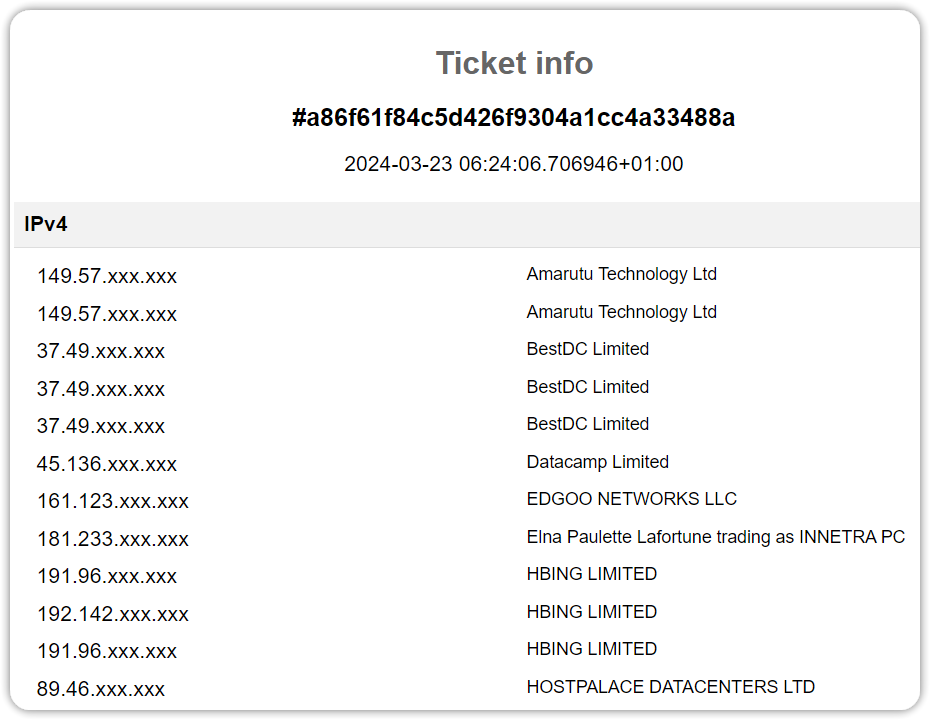
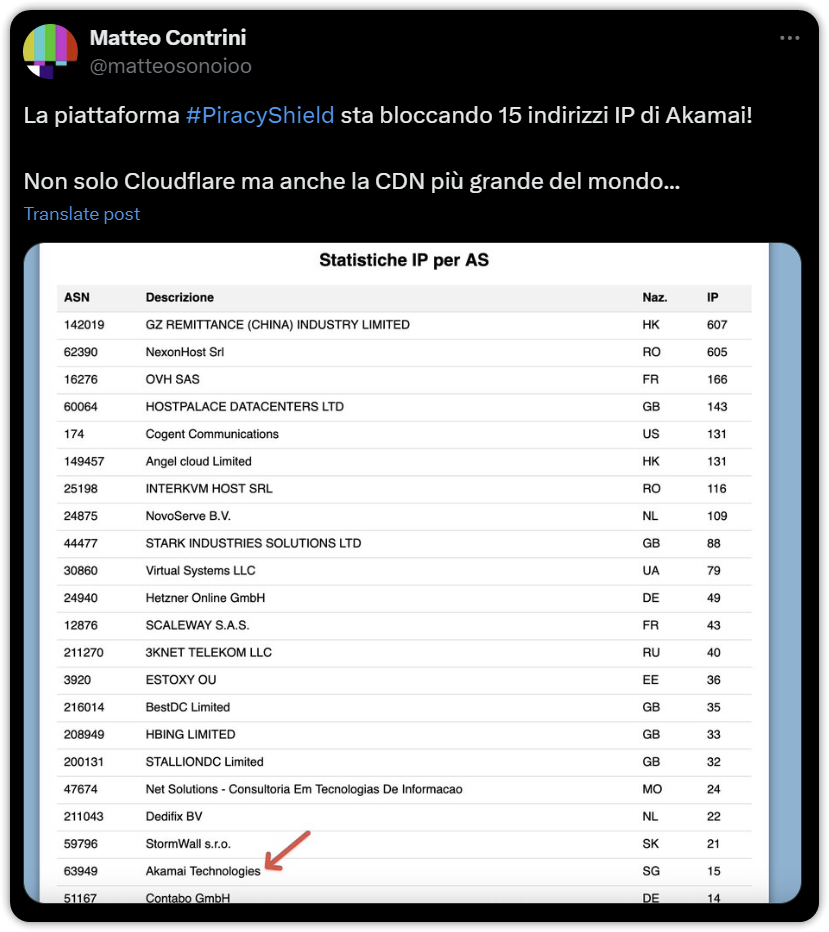


 CDN provider Cloudflare is one of the leading Internet companies, providing services to millions of customers large and small.
CDN provider Cloudflare is one of the leading Internet companies, providing services to millions of customers large and small. Earlier this year Texas-based model
Earlier this year Texas-based model 