-
 chevron_right
chevron_right
To guard against cyberattacks in space, researchers ask “what if?”
news.movim.eu / ArsTechnica · Friday, 5 July - 18:34

Enlarge / Complex space systems like the International Space Station could be vulnerable to hackers. (credit: NASA )
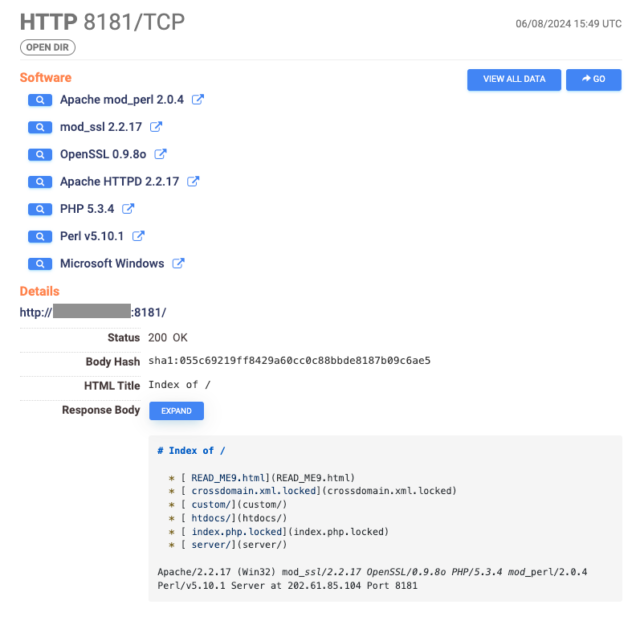
If space systems such as GPS were hacked and knocked offline , much of the world would instantly be returned to the communications and navigation technologies of the 1950s. Yet space cybersecurity is largely invisible to the public at a time of heightened geopolitical tensions.
Cyberattacks on satellites have occurred since the 1980s , but the global wake-up alarm went off only a couple of years ago. An hour before Russia’s invasion of Ukraine on February 24, 2022, its government operatives hacked Viasat’s satellite-Internet services to cut off communications and create confusion in Ukraine.
I study ethics and emerging technologies and serve as an adviser to the US National Space Council. My colleagues and I at California Polytechnic State University’s Ethics + Emerging Sciences Group released a US National Science Foundation-funded report on June 17, 2024, to explain the problem of cyberattacks in space and help anticipate novel and surprising scenarios .